This Guide
This guide is intended for the average home user. It uses simple language and summarizes steps, actions, and risks. It is for educational purposes only. Please do not use it to break the law. It may contain some technical errors or linguistic mistakes. Please report them to me so that I can improve the guide. This guide explains the importance of securing your wireless network and the risks of leaving it vulnerable. It is not about how to secure the devices connected to your network. Instead, it focuses on how to secure the network itself, such as by changing the default password, enabling encryption, and creating a guest network. I hope this guide helps you keep your home network safe.
Introduction
The increasing popularity of smart home devices has led to a growing number of wireless networks in our homes. While this convenience comes at a price, as wireless networks are more vulnerable to attack than wired networks. This guide aims to provide a simple and easy-to-understand guide for the average home user to add more layers of security to their wireless network and improve their privacy. The first version of this guide was in PDF format and Arabic, but I thought that making it in the form of a one-page website accessible from any device without downloading anything would be more appealing and easier to use. This would also make it easier to translate the guide into more languages to help more people secure their networks and privacy. It is important to note that no network is 100% secure, but by following the tips in this guide, you can make it more difficult for hackers to access your network and your data.
Contents
- Router
- Access Control
- Network Name
- Authinication Encryption
- Wifi Protected Setup
- MAC Filtering
- Risks
- Conclusion
Router
The starting point for securing your home WiFi network is the router.
Most modern home routers are actually three devices in one: a
Modem,
a
Router, and a
Wireless Access Point. For simplicity, I will call it a router throughout this guide. A
router is the gateway between your local network and the internet. It is
responsible for routing traffic between your devices and the internet.
Most routers come with preconfigured firewall settings to block
malicious attacks and unauthorized connections from the internet.
However, there are other settings that you can configure to further
secure your network. If you are in the market for a new router, I
recommend doing some research to read reviews and learn about any known
issues or vulnerabilities. You can use a search phrase like TD-W8970
Vulnerability to find information about specific routers. If you already
have a router, it is also important to check for any known issues or
vulnerabilities and to update the firmware if there are any updates
available.
There are two main ways to connect to your router's settings:
Using a web browser
Most routers have a web-based interface that you can use to configure the settings. To do this, you will need to know the router's IP address. This address is usually printed on the back of the router.
Using a mobile app
Many routers also have mobile apps that you can use to configure the settings. This is a convenient option if you do not have a computer or if you prefer to use a mobile device.
This can be done through 2 ways:
Local Access
Local Access means connecting to your router from your local network. In other words, from any of the devices that are connected to your WiFi network or from any device connected to your router via a LAN cable. This is the default way you should use and the more secured than Remote Access method. There are sub methods under Local Access to connect to the router, but the best and simple way for a home user is to connect to the router via the web interface meaning you connect to the router using your internet browser (such as Chrome, Firefox, Safari, and..ehm..Internet explorer or Microsoft Edge) and you do so by typing the Local Internet Protocol Address (Local IP for short) in the address bar of the browser and most routers use the IP "192.168.1.1" or "192.168.1.254" out of the box, but if you don't get to a page using those 2 addresses, then review your router's manual. Some devices will have the option to only allow devices connected to the router via the LAN cable to get to the router settings and most routers will come with a short cable that you can use for this purpose. You should enable this option if it exists to limit the access to the router's settings page and use the cable whenever you need to access it.
Remote Access
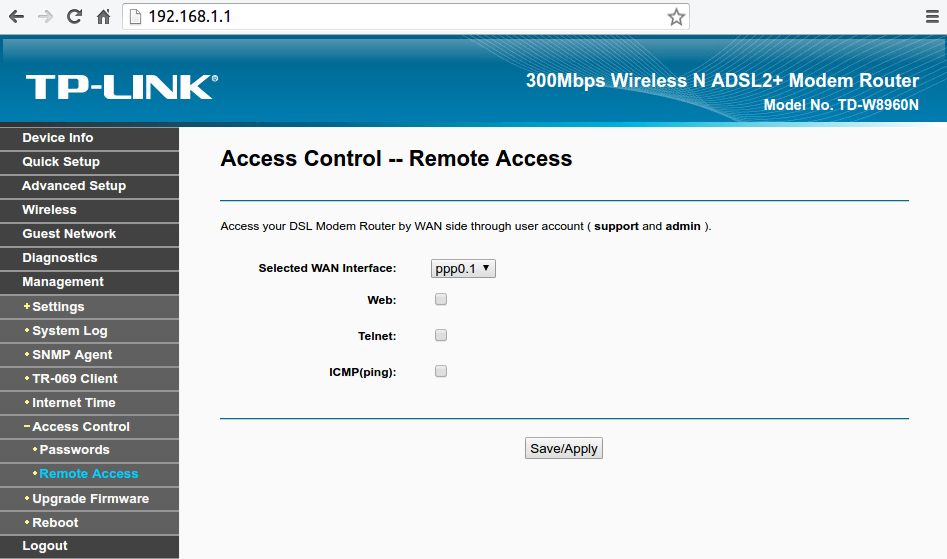
If the router is a gateway, then as you can reach it from the local network, you can reach it from the other side. why? maybe you are traveling or away from home, but need to modify the settings or simply you are facing some issues and your ISP (Internet Service Provider) needs to access the router to see whats the problem while your on the phone with them rather than wait for a home visit. No matter what the reason, the option is there and you need to disable it whenever you don't specifically need it. When you want to use this method to access your router from outside your local network, You would use the router's "Public IP Address" rather than the local address (such as 192.168.1.1) and you can search google for "What is my IP address" to find out your public IP address. Keep in mind that some ISP will change your public IP address from time to time if they don't provide you with a static IP address. All of these options will be under a section called "Access Control" in the router's web interface page.
Access Control
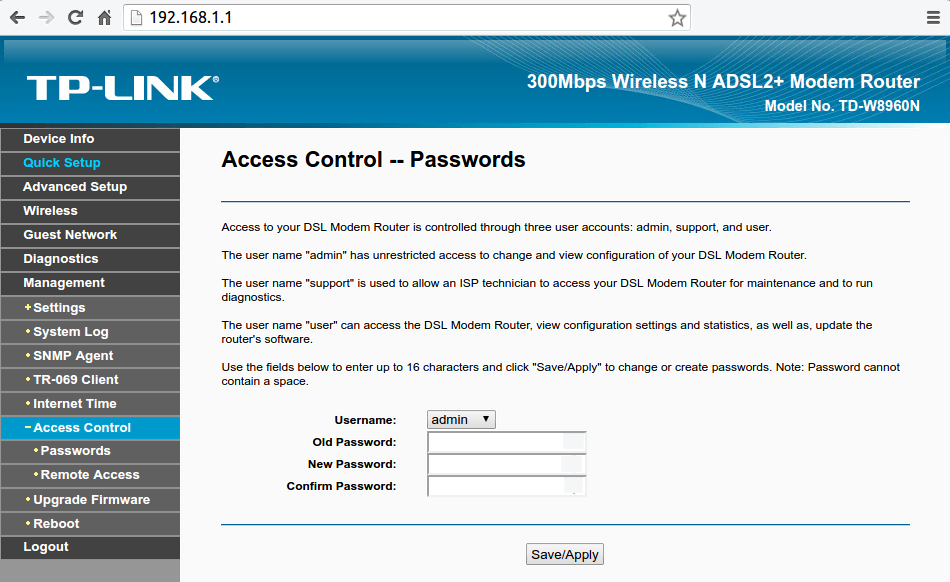
After connecting to the router's settings page, You will be asked for a
username and a password.The default username and password are usually
"admin" for both. You can find the default password in your router's
manual or by searching the internet for your router's model and "default
password". The first thing you should do after logging in, is change the
default username and password to something else, because as you guessed,
everyone would know and try them if they could reach the router's page.
You would be amazed by how many routers are still using the default
credentials and accessible from the internet through the remote access
option which are even periodically cataloged by search engines such as
Shodan. You should use a strong, unique password that have no meaning to you
or in the language such as "bwpFW93F#fm20BN" or "HeLuWK2038Be30" and if
Your router allows You to change the username, You should change it from
"admin" to anything else and preferably not your name or a name that has
any connection with you, if possible. You should also make sure that if
Your router comes with hard-coded users such as "user" and "support",
that You change the password for those as well.
 The layout and the naming of sections could vary from router to router,
but you should be able to figure out what you are looking for in a
little time with the help of this guide and your router's manual or of
course, the internet. Under this section (Access Control) You will also
find the remote access option and should disable it if you don't need
it. All the sub option under remote access should be disabled and
enabled only when needed for a short amount of time.
The layout and the naming of sections could vary from router to router,
but you should be able to figure out what you are looking for in a
little time with the help of this guide and your router's manual or of
course, the internet. Under this section (Access Control) You will also
find the remote access option and should disable it if you don't need
it. All the sub option under remote access should be disabled and
enabled only when needed for a short amount of time.
Network Name
Naming Your WiFi with a name that can lead back to You is not really
safe because it provides an easy way for a potential attacker who might
be looking for You specifically especially if You live in an urban area.
Or could simply provide someone who is looking to gain access to the
network with easy information that could be leveraged to give him
access, for example a neighbor who might know your kids name and finds
your WiFi network name could try Your kids names for the password..or
your phone number, pet's name..etc.
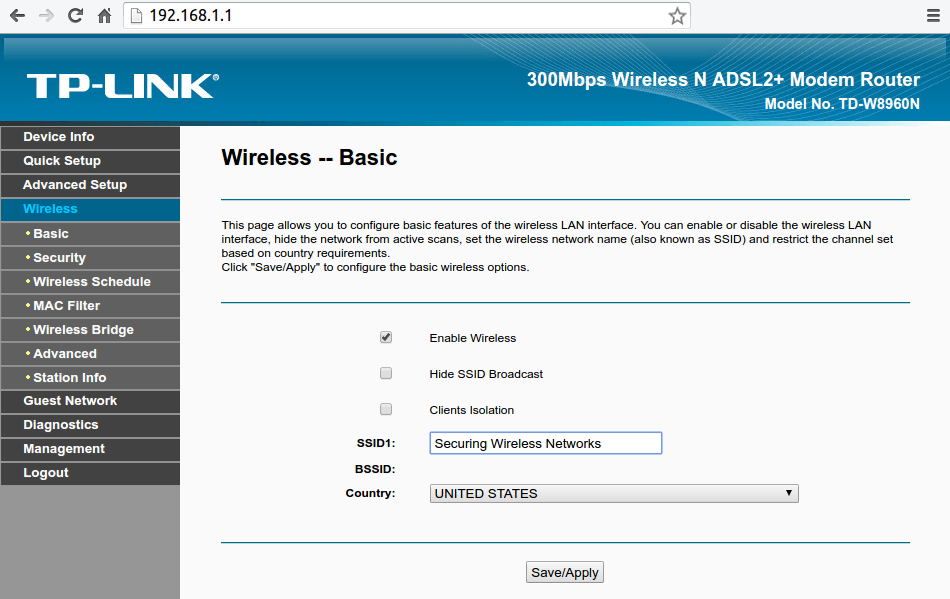 You
could also choose to "Hide SSID Broadcast" (SSID simply means the WiFi network name) so that when someone is looking for available WiFi networks will not
see that Your WiFi exists and Your devices who already connected to the
network before would connect normally as usually and new devices can
easily connect by choosing "Other Networks" or "Connect to a hidden
Network" when trying to connect. This option adds a good layer of
security especially to deter amateurs or just those are looking for a
free internet access, but a more professional attacker will be still
able to see Your network. As a good measure, You shouldn't leave the
WiFi name (SSID) with the default value because it would give easy info
to amateurs trying to get access to your network by figuring the
device's default passwords or services and even vulnerabilities if they
exist. Some ISP that provide the router for You can sometimes
preconfigure it to broadcast their name which is an easy way to gather
info about You or the network. However, every router has a unique ID
that is called "MAC Address" and that's short for "Media Access Control Address" which will allow a more advanced attacker to know the device's
manufacture at least. Your router could have an option called "Clients
Isolation" or something similar which will prevent the devices connected
to the router or on the network from communicating with each other and
this is a good measure in case someone did breach your network, but this
means you won't be able to connect to your chromecast for example or
your WiFi enabled coffee maker.
You
could also choose to "Hide SSID Broadcast" (SSID simply means the WiFi network name) so that when someone is looking for available WiFi networks will not
see that Your WiFi exists and Your devices who already connected to the
network before would connect normally as usually and new devices can
easily connect by choosing "Other Networks" or "Connect to a hidden
Network" when trying to connect. This option adds a good layer of
security especially to deter amateurs or just those are looking for a
free internet access, but a more professional attacker will be still
able to see Your network. As a good measure, You shouldn't leave the
WiFi name (SSID) with the default value because it would give easy info
to amateurs trying to get access to your network by figuring the
device's default passwords or services and even vulnerabilities if they
exist. Some ISP that provide the router for You can sometimes
preconfigure it to broadcast their name which is an easy way to gather
info about You or the network. However, every router has a unique ID
that is called "MAC Address" and that's short for "Media Access Control Address" which will allow a more advanced attacker to know the device's
manufacture at least. Your router could have an option called "Clients
Isolation" or something similar which will prevent the devices connected
to the router or on the network from communicating with each other and
this is a good measure in case someone did breach your network, but this
means you won't be able to connect to your chromecast for example or
your WiFi enabled coffee maker.
Authinication Encryption
Still to this day, this is one of the biggest problems and security
issue when it comes to WiFi. Some home users would simply ignore this
security measure for some reason or another. According to "Wigle" which is a database for WiFi networks gathered through "Wardriving", there are 19,716,016 WiFi network out of 290,179,693 widely open for
anyone to access. Those include public hotspots and free WiFi, but also
home networks that their owners don't care, or don't know better. Its
Authentication Encryption so its not network encryption. It simply means
that the method the password to the WiFi network is encrypted with
before a device asking to join the network provide this password to the
router to prove that the device is allowed on the network. If you use a
weak encryption, then someone monitoring this operation could easily
capture and decrypt the password. In general there are 4 settings:
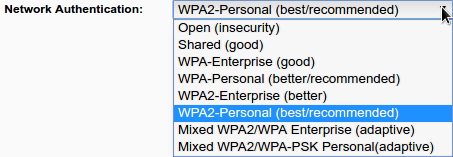
Open
WEP
WPA
WPA2
Open
Do not leave your WiFi network open. This is a security risk, as anyone could connect to your network and access your devices and data. If you want to share your network with others, it is better to use strong encryption and a password that is difficult to guess. You can also enable the "Guest Network" option on your router, which will create a separate WiFi network for guests that is isolated from your main network.
Wired Equivalent Privacy
Or WEP for short, has a misleading name. Basically, it's as good as
leaving the WiFi network Open. WEP is a security protocol for wireless
networks that was developed in the late 1990s. It is the oldest and
weakest Wi-Fi security protocol. WEP uses a 64-bit or 128-bit key to
encrypt data, but this key can be easily cracked by attackers using
tools like
Aircrack-Ng.
In fact, WEP passwords can be cracked in as little as two minutes. Some
old routers use this setting by default.
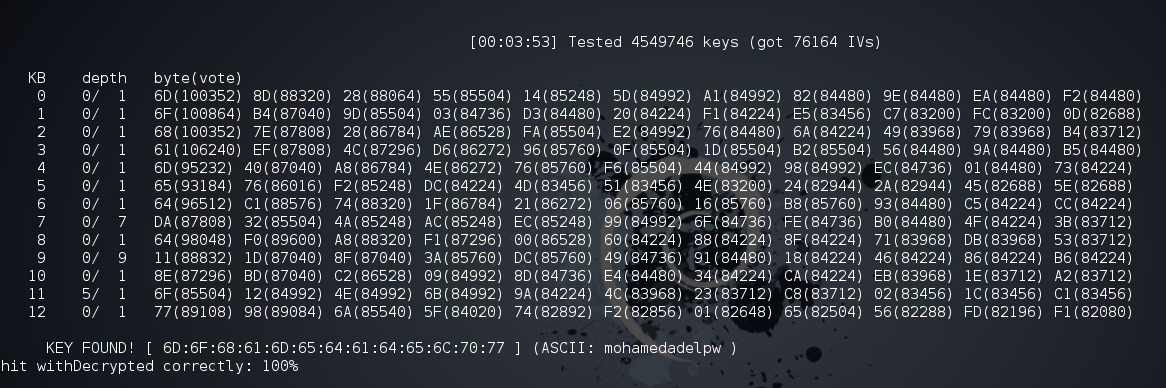
WPA and WPA2 Protocols
After it was discovered how vulnerable WEP was, the
WiFi Alliance
quickly moved in the direction of implementing a more secure way for
authentication and introduced WPA in 2003 as a quick fix for WEP and to
pave the way for the more secure and complex protocol; WPA2 that became
available in 2004. So the only way to have a good and powerful
authentication encryption is to use WPA2 with a good password and
without enabling WPS. As always, WEP and WPA are kept
as options to provide backward compatibility. WPA and WPA2 can still be
broken if You use a week and/or common passwords and in case of targeted
attack, a password that is personal like Birth-dates, anniversaries,
names ..etc. so using WPA2 and using a password like "apple" or
"123456789" is simply idiotic. The best practice is to use WPA2-personal
(or WPA2 with AES, CCMP, AES-CCMP) which differs from router to router,
but means the same thing. AES or (the Advanced Encryption Standard) is a specification for the encryption of electronic data. You can
read more about how encryption work and such, but to make things simple,
let's say that AES for example uses an algorithm that calculate or
cipher the password into a hash or ciphered string and that ciphered
string can't be recalculated back to the original word so encrypting the
word "apple" with AES gives us "2fsGsNtyFu8Y16fWGLMxMA==" (read more about Cryptographic hash function) so if an attacker got hold of the hashed string, he/she can't turn it
back to "apple", but the attacker could use the same encryption method
to encrypt random words or passwords and then compare the strings
generated to the encrypted password he/she got. Attackers will use
AirCrack-ng to capture the handshake between the router and the devices
connecting to it and can use 2 attacks methods to "crack" the WPA2
password. Those 2 methods are
Dictionary attack
and
Brute-force attack
and they both combined, target weak, common, meaningful, and short
passwords.
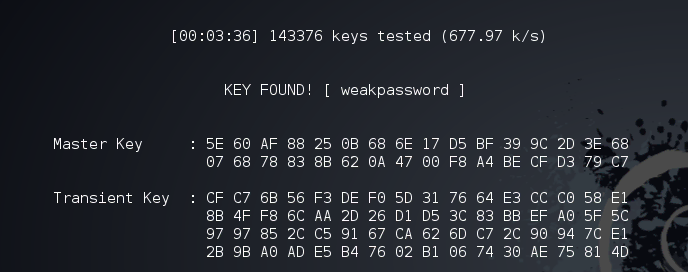
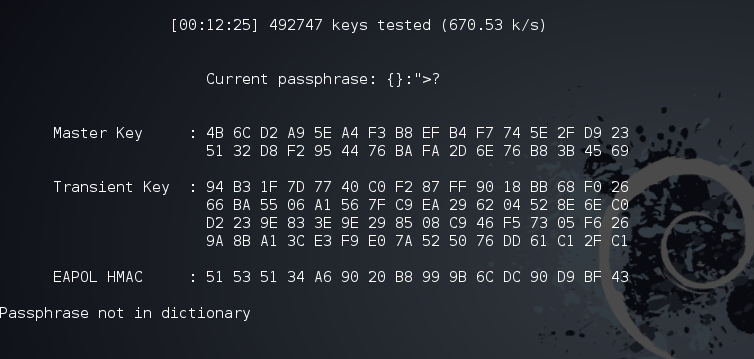 This means
that You have to use a good powerful password and follow the
best practices
when it comes to choosing your WiFi password (and any password for that
matter) so you should long password with letters, numbers, and special
characters and they should mean nothing both personally and generally
like "HeLuWK2038Be30" or "bwpFW93F#fm20BN" or "LttSw2F44dEOO0" and
so on.
This means
that You have to use a good powerful password and follow the
best practices
when it comes to choosing your WiFi password (and any password for that
matter) so you should long password with letters, numbers, and special
characters and they should mean nothing both personally and generally
like "HeLuWK2038Be30" or "bwpFW93F#fm20BN" or "LttSw2F44dEOO0" and
so on.
Wi-Fi Protected Setup
Or WPS for short,
is a network security standard to create a secure wireless home
network, however it created a less secure wireless home networks, because the
PIN method which is implemented in mostly all modern home routers could
fail against brute-force attacks no matter what the WPA2 or the WiFi
password is. If WPS is enabled, the network could be breached within 2
days of brute-forcing and in reality and most cases, this could happen
under 4 hours or if Your router uses certain chips from makers including
Ralink, MeddiaTek, Realtek and Broadcom, could be cracked within a
minute and 30 seconds with an attack called "Pixie Dust attack
and there are many tools to automate these types of WPS attacks,
Reaver
being the most known. Most routers and APs come with WPS pre-enabled and
should be disabled by the home user because how vulnerable it makes the
network. 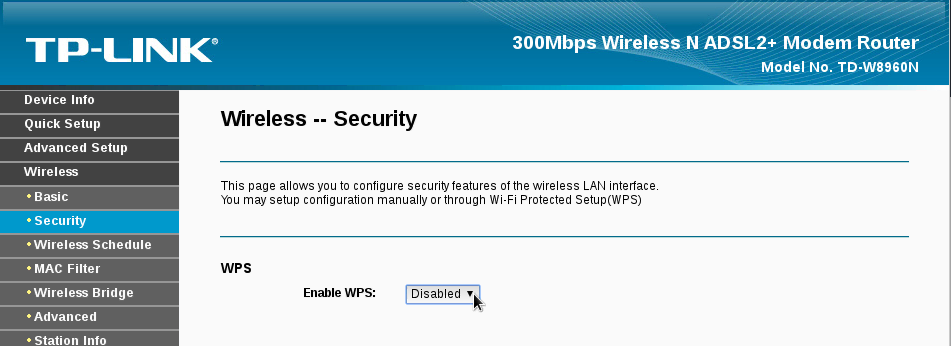
MAC Filtering
Media Access Control Address (MAC address
for short) is a unique identifier assigned to network interfaces.
Simply, it is a serial number that belongs to the wireless chip in Your
devices being a laptop, tablet, or mobile phone and as the title
implies, MAC filtering is an option to create a list of MAC addresses to
either be allowed or denied from the network and the best practice is to
create a list with all the devices that will connect to the WiFi network
and only allow those devices using the MAC filtering option. Keep in
mind that MAC addresses could be
spoofed, but MAC filtering is just another layer of protection to make it
harder for an attacker to gain access to the network. You can Google how
to find a device MAC address under Your OS (Windows,
OS X,
Linux,
Android,
IOS) or You can find out the connected devices to your network through
your router settings by searching for "Devices Info" or "DHCP" sections
or simply googling with your device model like
How to find connected clients on TD-W8960N. You can also use network scanners like
Nmap or
Fing.
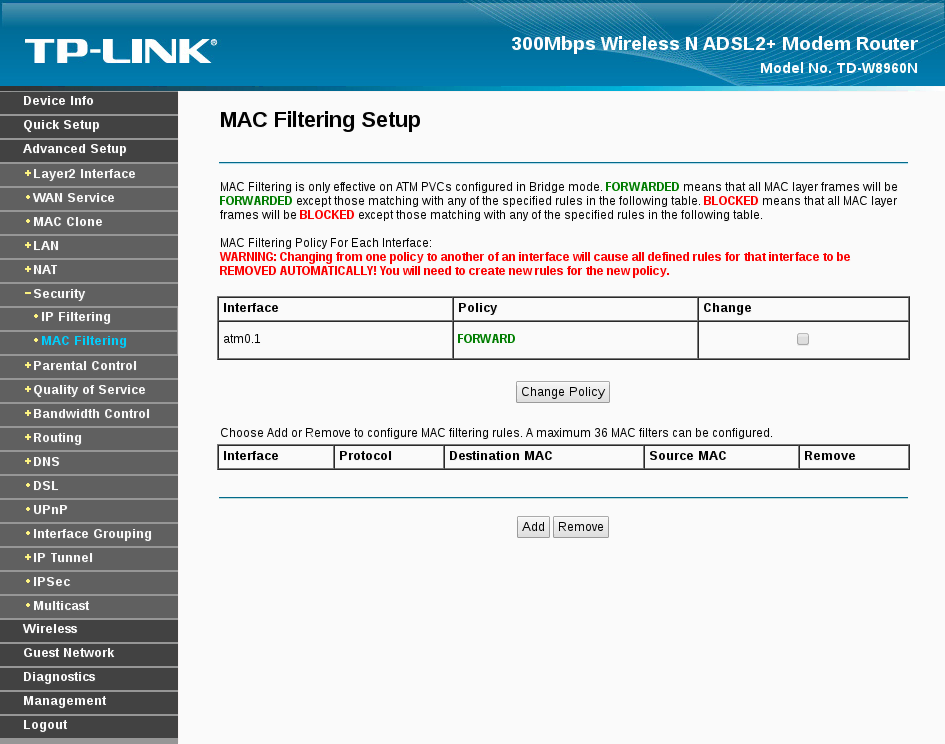
Risks
You might think that's alright if someone have access to your WiFi network and You are all about sharing that internet with others, helping them connect, but the risks are far more dangerous than you might think. a Person could just mess with Your network settings for fun or as a prank. another could use Your network to access the internet to download/upload illegal materials implicating You. an online drug dealer could be connecting to the TOR network through Your WiFi. All of this isn't so dangerous after all. a more malicious person could do a lot more targeting You, Your Privacy, Data, Photos, and more.
Social Engineering
Social Engineering
is psychological manipulation of people into performing actions or
divulging confidential information. It is a type of art and highly
depends on the attacker's personality and ability, but also on the
background information he/she can use to convince manipulate You and an
attacker can figure out a wealth of information just by being connected
to your WiFi. It's easy to figure out the type of devices You have in
Your home and the names of people using them and can leverage all this
information to even get more through social media and the internet using
simple tools and techniques.
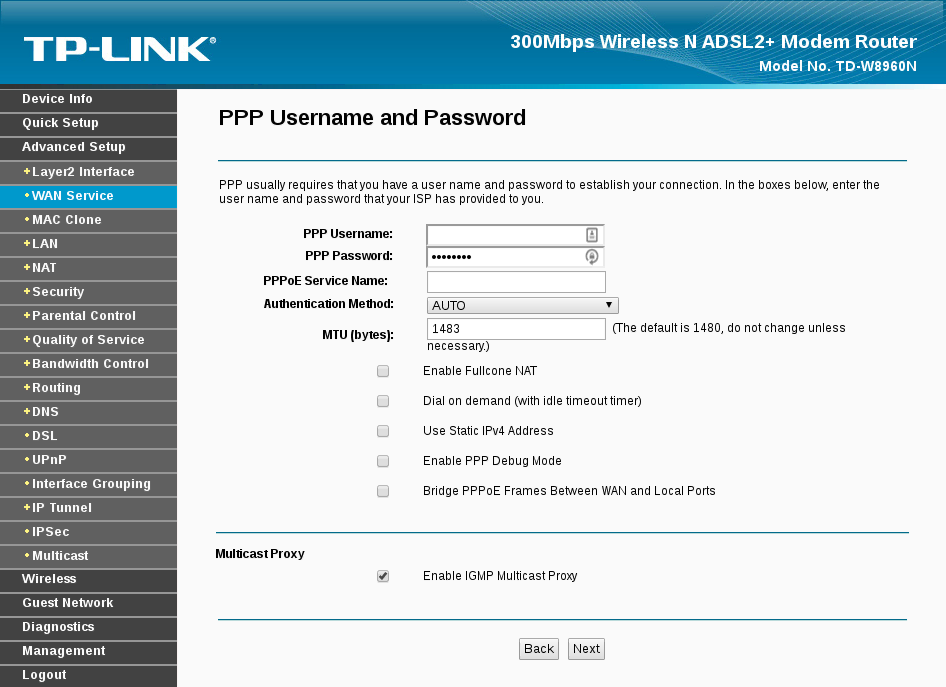
 Sometimes, Your router settings might contain some personal information
such as your ISP user-name and password and such. Some ISP even let
anyone browsing their portal through the network, to access the
subscription settings without authentication, but that is rare nowadays.
Sometimes, Your router settings might contain some personal information
such as your ISP user-name and password and such. Some ISP even let
anyone browsing their portal through the network, to access the
subscription settings without authentication, but that is rare nowadays.
 You could be even using the same WiFi password for Your online accounts
(shame on YOU) which once cracked, the attacker might use to gain access
to Your accounts or could use a tool like
Firesheep
and other to gain access to Your accounts.
You could be even using the same WiFi password for Your online accounts
(shame on YOU) which once cracked, the attacker might use to gain access
to Your accounts or could use a tool like
Firesheep
and other to gain access to Your accounts.
Network Monotiring
A malicious person on the network can simply sit there monitoring
everything that happens on the network. Using attacks such as
Man-in-the-middle attack
putting him/herself between all the communication going between all the
devices and the internet and possibly even altering them, serving You
with spoofed sites to gather your passwords, banking information and
even trick You to install malware that could help him/her take full
control of Your device (Flash needs to be updated? sure install
updates). The attacker can also "sniff" or eavesdropping on Your
communications capturing Your chats, passwords, photos, browsing habits,
and more.
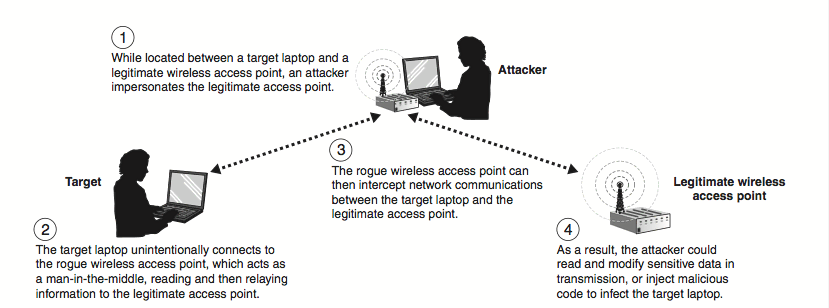
Exploiting
Exploiting could sound more difficult than it really is. Most likely, an
attacker can connect to different devices on the network using default
user-names and passwords or even without needing them, because home
users don't know any better. You have this monitoring camera that could
only be accessed from the local network, so who needs a user-name and a
password, right? WRONG! You should really make sure that every device
and service on the network requires authentication and that the default
credentials are changed to something more secured and that they don't
face the outside network (the internet) if you don't really need to
access them from outside Your home network, same as the router or they
can be used in botnets to launch attacks such as DDOS attack (like the
one launched on October 21st 2016). A simple search on
Shodan would yield
a lot of webcams, security cams, storage devices, and more "smart"
devices connected to the internet and available to everyone without any
security measures or with the default credentials that can even allow an
attacker to gain access to your WiFi network without targeting Your
router or AP. Exploiting is even more dangerous than that, because a lot
of devices and services might contain vulnerabilities that allows the
attacker to gain access. These vulnerabilities could be known to the
public and might already have updates or patches to fix them, but the
home user didn't update the devices, or they could be unknown yet to the
public and only the attacker (or a few people) knows about them and
those are called
Zero-day vulnerabilities
and there are no updates or patches available yet to fix them. That's
why you should periodically update Your OS (Operating systems),
applications, and the devices firmwares such as routers, security cams,
and Your smart fridge.
Conclusion
By following the tips in this guide, you can improve the security of your home WiFi network and make it more difficult for hackers to access your devices and data.
- Choose a strong password for your WiFi network. The password should be at least 12 characters long and include a mix of uppercase and lowercase letters, numbers, and symbols.
- Use WPA2 encryption. This is the most secure encryption protocol available.
- Hide your WiFi network's SSID. This will make it more difficult for hackers to find your network.
- Only allow trusted devices to connect to your network. You can do this by using MAC filtering.
- Keep your router's firmware up to date. Router manufacturers often release security updates to fix vulnerabilities.
- Be careful what you connect to your network. Only connect devices that you trust.
- Monitor your network for suspicious activity. There are a number of ways to do this, such as using a security app or service.
Here are some additional tips:
- Don't use your WiFi network name to reveal any personal information about yourself, such as your name, address, or phone number.
- Don't leave your WiFi network open to the public, even if you only intend to share it with a few people.
- Change the default password for your router. The default password is usually easy to guess.
- Disable remote administration for your router. This will prevent unauthorized people from accessing your router from the internet.
- Keep your router in a secure location. Don't place it in an area where it is easily accessible to unauthorized people.
